A month ago I had to upgrade one of our customers vCenter from 5.0 to 5.5. We were suppose to run pilot project and upgrade was part of the requirements. However, upgrade was pretty smooth with no unexpected issues or whatsoever. Of course, when I had all components installed I decided to do quick check, though. Login with C# client did not indicate any unusual behavior or possible error, but when open Web Client I saw error message that Web Client could not connect vCenter.
Digging around the log files, I found out that VMware self-signed certificate is 512bits rather than supported 1024/2048bits. Environment was upgraded few times in the past and seems like vCenter installer did not check whether this certificate meets new version requirements.
With finding the cause first logical step was to search for VMware KB , and of course, I found few
| After upgrading to vCenter Server 5.5 Update 1, logging in to vCenter Server reports the error: Failed to verify the SSL certificate | KB2074942 |
| Configuring CA signed certificates for vCenter Server 5.5 | KB2061973 |
| Configuring CA signed SSL certificates for vSphere Update Manager in vCenter Server 5.1 and 5.5 | KB2037581 |
| Implementing CA signed SSL certificates with vSphere 5.x | KB2034833 |
| Creating certificate requests and certificates for vCenter Server 5.5 components | KB2061934 |
| Configuring CA signed SSL certificates for the Inventory service in vCenter Server 5.5 | KB2061953 |
| Configuring CA signed certificates for vCenter Server 5.5 | KB2061973 |
| Implementing CA signed SSL certificates with vSphere 5.x | KB2034833 |
| Configuring CA signed SSL certificates for the Inventory service in vCenter Server 5.5 | KB2061953 |
So, in order to get this resolved, I had simply to regenerate self-signed certificates and re-register all vCenter components. Pretty easy, isn’t :D. Bellow are the steps I took to fix vCenter self-signed certificates.
Before you start bear in mind following :
- Certain vCenter Services will be unavailable during process.
- Replacing the vCenter Server certificate may result in ESXi Hosts becoming disconnected from vCenter Server. You might need to reconnect manually some of the hosts.
- Plug-in components such as Update Manager, Site Recovery Manager, vCloud Director, Horizon View, etc, may need to be re-registered with vCenter Server.
- Do not stop vCenter nor any of the it’s components services yourself,SSL Certificate Automation Tool will do that for you during the process.
- Important: Ensure that you are using OpenSSL Version 0.9.8. If you are using a different version, the SSL implementation would fail.
As first step, we need custom cfg file. In Notepad create new file and call it openssl_config.cfg and add the following lines:
|
1 2 3 4 5 6 7 8 |
[ req ] default_bits = 2048 default_keyfile = rui.key distinguished_name = req_distinguished_name encrypt_key = no prompt = no string_mask = nombstr req_extensions = v3_req |
|
1 2 3 4 5 6 7 |
[ v3_req ] basicConstraints = CA:FALSE keyUsage = digitalSignature, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth, clientAuth subjectAltName = DNS: <span style="color: #ff6600;">hostname</span>, IP:<span style="color: #ff6600;">X.x.x.X</span>, DNS:<span style="color: #ff6600;">hostname.domain.com </span> |
|
1 2 3 4 5 6 7 |
[ req_distinguished_name ] countryName = <span style="color: #ff6600;">US</span> stateOrProvinceName = <span style="color: #ff6600;">NY</span> localityName = <span style="color: #ff6600;">New York</span> 0.organizationName = <span style="color: #ff6600;">VMWare</span> organizationalUnitName = <span style="color: #ff6600;">vCenterServer</span> commonName = <span style="color: #ff6600;">hostname.domain.com</span> |
Once, you’re ready save the file and lets begin with certificate generation. Open Command Prompt and go to OpenSSLfolder, located in “C:\Program Files\VMware\Infrastructure\Inventory Service\bin“.
|
1 |
openssl req -new -nodes -out d:\temp\rui.csr -keyout d:\temp\rui-orig.key -config d:\temp\openssl_config.cfg |
|
1 |
openssl rsa -in d:\temp\rui-orig.key -out d:\temp\rui.key |
|
1 |
openssl req -text -noout -in d:\temp\rui.csr |
|
1 |
openssl x509 -req -days 7300 -sha256 -in d:\temp\rui.csr -signkey d:\temp\rui.key -out d:\temp\rui.crt -extensions v3_req -extfile d:\temp\openssl_config.cfg |
|
1 |
openssl.exe pkcs12 -export -in d:\temp\rui.crt -inkey d:\temp\rui.key -name rui -passout pass:testpassword -out d:\temp\rui.pfx |
|
1 |
openssl pkcs12 -in d:\temp\rui.pfx -info |
|
1 |
openssl x509 -text -noout -in d:\temp\rui.crt |
Once the certificates and keys are created, you will need to create a PEM certificate chain. Open Notepad and create new file name it chain.pem save it in same location where certificates and keys are. Open rui.crt and copy content to chaim.pem and save it.
Now we are ready for the fun part. Locate SSL Certificate Automation Tool, unzip it and go to folder. In order to save some time and don’t type multiple times same things, we will need to edit ssl-environment.bat file. Open file in Notepad or any other editor and change following lines:
|
1 2 3 4 5 6 7 |
###Parameters for updating the vCenter Server SSL Certificate set vc_private_key=d:\temp\rui.key set vc_cert_chain=d:\temp\chain.pem ###Common parameters set sso_admin_user=administrator@vsphere.local set vc_username=DOMAIN\User ###Add here your credentials### |
Save the file and run ssl-updater.bat as Administrator.
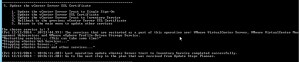
On “Main Menu” select 1.Plan Your Steps to upgrade SSL certificates to get detailed plan how to implement generated certificates.
Now we have the plan for re-establishing the trust between vCenter and it’s components.Let’s start with first step Update the vCenter Server SSL certificate.
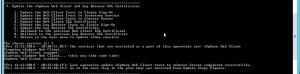
Go to Main Menu > Update the vCenter Server > Update the vCenter Server SSL certificate and follow the wizard.
Note: If you’re using SQL Express your Database password would be your domain admin or local admin password .Microsoft SQL Express support only Windows Authentication.
If you see error ERROR: The leaf certificate doesn’t have any CN or subjectAltName that matches the public address of the current machine. Rejecting the chain. To skip this
check, set the `ssl_tool_no_cert_san_check’ environment variable to 1.
Add following “set ssl_tool_no_cert_san_check=1″ to lines 680 and 759 and re-open ssl-updater.bat
Next step is to re-establish the trust between vCenter and Inventory service. From Main Menu > Update the vCenter Server SSL certificate > Update vCenter Server trust to Inventory Service
Next step is to re-establish the trust between Inventory Service and vCenter. From Main Menu > Update Inventory Service > Update the Inventory Service trust to vCenter Server.
Next step is to re-establish the trust between vCenter and vCenter Orchestrator. From Main Menu > From Main Menu > Update vCenter Orchestrator > Update vCenter Orchestrator trust to vCenter Server
Next step is to re-establish the trust between vCenter and WebClient. From Main Menu > Update vSphere Web Client and Log Browser > Update vSphere Web Client trust to vCenter Server
Last step in the process is VUM .From Main Menu > Update vSphere Update Manager > Update vSphere Update Manager trust to vCenter Server
After you complete all steps, login to VMware Web Client and enjoy !
The whole procedure is time consuming,complicated and not well documented. If you want to change certificates for each one of vCenter components you can follow same steps.In next part I will describe how to work with CA certificates.







just perfect! thank you!
Glad it did the magic for you !
Running into inventory service problems with the methods. Even with repointing – have you encountered this?
Mike, never faced issue with inventory service. Can you give elaborate a bit more on this?
Absolutely awesome tutorial – Excellent!!! It worked for me!
Glad it did the magic for you !
Mike – I’m getting the following:
———- C:\PROGRAMDATA\VMWARE\VMWARE VIRTUALCENTER\VPXD.CFG
[Mon 05/09/2016 – 22:18:22.79]: Validating the input parameters…
STATE : 4 RUNNING
HTTPError: Unable to open or read page.
HTTP Error 401: basic auth failed
[Mon 05/09/2016 – 22:18:46.46]: “Cannot log in to vCenter.”
[Mon 05/09/2016 – 22:18:46.47]: The vCenter certificate update failed.
Any ideas? This is in a default vCenter 5.5 clean install – I’m also getting the same at a client site. So – I must be doing something wrong.
give it a try with this KB
Me too, same issue here. What KB 2042554 describes is a 503 error, doesn’t match our case.
Thank you very much, this resolved the issue with Migrating Assistance and the error vCenter cannot verified CA Certificate.
Glad it did worked for you, even though article is over two years old!
Hi ,
I am getting error : key file does not contain a private key or the private key is encoded using unsupported format . Supported key encoding schemes are : PKCS#1 and PKCS#8
Excellent tutorial. However when i got to the SSL updater it failed because the keysize was too small (1024). I therefore simply updated the default_bits setting in openssl.cfg to resolve this, deleted all the keys created in my temp folder and started again.
Also you need to make sure the d:\temp folder has been created before starting, in my case i made one on c:\.
Finally one my system the “openssl_config.cfg” is actually called “openssl.cfg”, so i needed to update the commands accordingly.
Anyway thanks !
I’m glad it helped you out. There might be need to twick some things as the manual is few years old.
Thanks, this fixed my migration from 5.5 to 6.5
Pingback: Unable to migrate VirtualCeneter to 6.5 from 5.5. Certificate errors. – Tips and Tricks